Organizations are managing all kinds of users, devices, applications, and workplaces. While remote work and BYOD policies are driving greater productivity and creativity, they also pose significant challenges to security. One response to these challenges is a zero-trust approach to security.
Zero-trust architecture (ZTA) continuously verifies access before granting permissions, eliminating traditional network perimeters. This ensures secure access anytime, anywhere, across all devices.
Let’s dive into how zero-trust security solutions, enabled by Cisco, can be used to increase security resilience. For greater detail, be sure to watch our recent zero-trust webinar that contains insights from ZTA experts.
What is Zero-Trust Security?
The zero-trust approach is based on three fundamental principles:
- Never Assume Trust: All resources are considered external, and user trust is continuously assessed before access is granted.
- Always Verify: Identity must be correctly verified regardless of device, application, or network.
- Enforce Least Privilege: Restrict resource access to necessary privileges only to ensure protection.
With these principles in place, your organization is safeguarded against cyberattacks and optimized for productive remote work. With Zero Trust, organizations experience nearly 2X fewer security incidents—reducing breach rates from 74% to 38%.
Modernize Outdated VPN Models with ZTA
The traditional security model puts applications behind a firewall and allows users to access those applications through the VPN. This model relies too heavily on assumed device authorization and doesn’t leverage a ‘least privilege’ approach.
With a Cisco-powered zero-trust framework, applications are migrated to a cloud-based zero-trust network access (ZTNA) at a controlled pace, preventing work disruptions and enabling a seamless transition. Cisco offers a single client that combines multiple functions to create a unified approach to security that easily enables zero-trust maturity and transparency.

For clients with legacy applications that still require VPNs, Cisco offers VPN-as-a-service to ensure those applications are protected and are easily integrated into the wider security ecosystem.
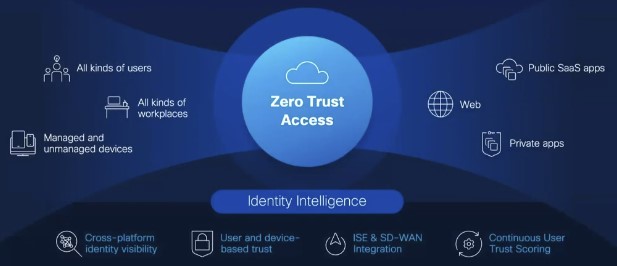
Identity Intelligence with Zero Trust Powers User Security
Over 80% of security breaches leverage identity as a key component, highlighting the need for an identity-based approach to security. At the core of a Cisco Zero Architecture solution is identity intelligence. This AI-powered functionality protects identities through:
- Cross-Platform Identity Visibility: Understand user identity across devices, applications, and platforms, and provide secure privilege-based access.
- Multi-Factor Authentication (MFA): Create access friction to reduce unauthorized network entry.
- Continuous User Trust Scoring: Employ trust scoring and adaptive authentication policies to determine access based on risk levels.
Take a Simplified Approach to IT Management with ZTA
78% of organizations report that using a high number of security tools drives cybersecurity complexity. A cloud-based ZTA simplifies IT while ensuring secure access—anytime, anywhere. This significantly reduces IT burdens, creating cost savings and freeing up resources for more effective issue resolution.
A Cisco zero-security framework is optimized for support and integration across any device, including Windows, Linux, Mac, and Chromebook laptops. It also has seamless integration with Apple and Samsung mobile devices which not only empowers effective mobile work – it even saves battery power too.
Start Your Journey Towards Zero-Trust Resilience
With its ‘never assume trust’ foundation and cloud-based framework, zero-trust architecture is driving resilience and adaptability in organizations’ IT landscapes. With cybersecurity threats at an all-time high and constantly expanding, zero-trust isn’t just a nicety – it’s a necessity.
Watch our full zero-trust webinar to move your security strategy forward. Long View offers several free security inspections to jumpstart your transition towards zero-trust maturity. With a team of over 100+ Cisco-certified professionals, we are uniquely qualified to support your zero-trust journey. Contact our team to get started.


Subscribe to our newsletter for the latest updates.